Why cyber hygiene should be a top priority
Cyber attacks on the rise

With cybercrime damages expected to cost the world $10.5 trillion annually by 2025, this evolving issue shouldn’t be taken lightly. Threat actors continue to develop new ways to attack organizations, though only 60% of public transit agencies have a cybersecurity strategy in place.
That’s where cyber hygiene comes in.
By maintaining the security and upkeep of your organization’s systems, devices, and procedures – whether that’s through secure corporate communication or purchasing cyber liability insurance, among other options – you greatly lower your chances of falling victim to a cyber attack.
The initial step: supply chain risk management
Cyber threats are lurking everywhere. That’s why it’s important to do everything you can to limit your organization’s vulnerabilities. Through supply chain risk management, you can maintain a strong network of trusted vendors while securing your end-to-end supply chain. This strengthens your organization’s physical security and helps protect against potential cyber attacks.
It’s important to communicate and work closely with your partners and vendors, to get an in-depth understanding of their data and privacy protection policies. After all, the highest level of resilience against cyber threats isn’t achieved alone. It happens when everyone involved commits to upholding best practices.
You can establish this dialogue by asking your vendors and partners the following questions, which are discussed in detail on our Network of Trust page:
- How transparent are my vendors with vulnerabilities?
- Do my vendors prioritize security in the development of their products?
- Do they have a comprehensive strategy in place to close security gaps and vulnerabilities?
Asking these questions puts your organization in the best position to prevent, and in the worst case respond to, a cyber attack.
Detecting suspicious communications
Threat actors use social engineering campaigns – like phishing attacks or pretexting – to bait you into unknowingly providing sensitive information, giving them access to your private data. For that reason, ensuring that all your employees can effectively detect and avoid suspicious communication attempts is vital to your organization’s physical security.
While mistakes happen, keeping an eye out for unusual communication requests, and thinking before you click on any links or messages, are some of the ways that you can help to protect your organization against cyber attacks.
Providing consistent user education from the start
Since the repercussions of a cyber attack can have a long-lasting negative impact on your organization — whether it be in the form of a financial hit or data loss — providing consistent user education to your employees is an investment that goes a long way.
Educating your employees on cyber hygiene is an ongoing task that should begin during their onboarding. By explaining the importance of strategies like strong password selection, locking devices, and identifying social engineering attacks, your organization can limit the chances for human error while maintaining best practices.
Adding a layer of security with cyber liability insurance
There are as many as 12 different types of coverage available for cyber threats, which means that you’ll have to do some research before finding a cyber liability insurance package that can meet your organization’s needs. With cyber attacks on the rise, investing in the right package should be an essential part of your cybersecurity strategy.
Because such a wide range of options are available, reading the fine print is a key part of your insurance selection process, as that’ll determine the exact coverage that you’d receive in the case of a cyber attack.
Alongside a careful selection process, understanding the claims process for your package is important, to help prevent added confusion and stress in the case of a cyber attack.
While cyber liability insurance is a good way to help mitigate the financial risk of cyber attacks, vetting your vendors, partners, systems, and devices, and establishing an effective cyber risk mitigation plan are all equally-essential steps to protecting your organization against cyber attacks. Always remember that any vulnerability is one too many.
Good cyber hygiene is a team effort
Cyber hygiene isn’t only about securing systems and devices, but it requires time and attention to many aspects of your organization.
Because your physical security system is only as secure as the least trusted device connected to it, there isn’t much room for error.
Focusing on maintaining strong cyber hygiene through supply chain risk management, secure exchanges, user education, and cyber liability insurance are some of the key ways that you can protect your organization against evolving cyber threats.
Learn more about how to build a strong physical security foundation by checking out our Trust Center, which features a wide array of relevant information and resources at your disposal.
About Genetec
Genetec Inc. develops open platform software, hardware and cloud-based services for the physical security and public safety industry. Its flagship product, Security Center, unifies IP-based video surveillance, access control and automatic license plate recognition (ALPR) into one platform. This platform is used and trusted in various other industries, including traffic and transit.
This blog post is made possible by our great partner Genetec as part of the Transportation Cybersecurity and functional safety Forum, an initiative of Propulsion Québec and supported by the Quebec government.
Continue reading on this subject

Will industrial strategies chart a new course for the future of Quebec industries?
The Quebec economy—and more broadly the world economy—faces multiple challenges: the climate crisis, supply chain problems, labour shortages, inflation, etc. Quebec has an abundant supply of resources, know-how, and expertise; however, the next points on its agenda should include structuring, developing, and planning industrial activities.
Read more
Telematic Data: the Key to a Successful Energy Transition
Fleet managers are currently facing the colossal challenge of the energy transition, in order to meet legislative requirements and societal demands. For most carriers, both in the passenger transport sector and in the last mile delivery sector, this green shift has already begun.
Read more
Ambition EST 2030 : a roadmap for propelling Quebec to the forefront of the electric and smart transportation industry by 2030
Propulsion Québec, the cluster for electric and smart transportation, is announcing Ambition EST 2030, a roadmap for the electric and smart transportation (EST) industry developed in partnership with Deloitte.
Read more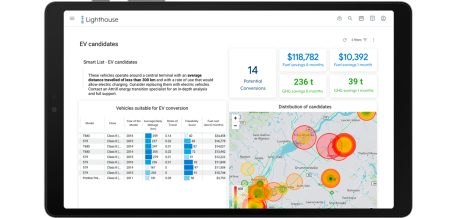
Energy transition, the challenge that is shaking up the trucking industry
The U.S. Department of Energy recently released a report containing a vehicle cost analysis for zero-emission medium and heavy-duty trucks.
Read more
The Mobility of the Future is Smart, Green, Inclusive and Healthy
Innovation is part of our Alstom in Motion 2025 strategy. It has brought us to where we are today, and we want to go even further. With the new scale and combined expertise, Alstom has doubled its innovation capacity and we will support this growth by doubling the financial investments in R&D, up to 600 million euros (875 million Canadian dollars) per year by 2024.
Read more
Astus – Proud to support IMPULSION MTL 2021
With more than 25 years of expertise in the field of vehicle telematics, Astus is now a key player in the energy and digital transition of mobility and transport.
Read more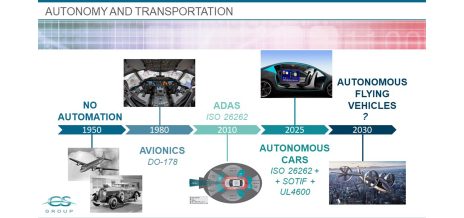
LiDAR and AI in autonomous vehicle commercialization and functional safety
The story of smart, autonomous transportation began nearly half a century ago. In the early 1980s, avionics systems started to replace more traditional mechanical and hydraulic systems through calculators and embedded software.
Read more
Is there a regulatory framework for location data?
Analysing location data can help service providers assess whether to boost services in one part of a city versus another, at a particular time of day or in preparation for an upcoming festival, for instance. However, the data used for these analyses is linked to individuals and makes it possible to identify them.
Read more
How to develop a successful strategy for your transition towards EVs
To this day, it is not uncommon to see a good number of companies relying on assumptions, sometimes non-global and inaccurate information reports in order to manage their vehicle fleet.
Read more
Five key Cybersecurity takeaways for the automotive industry
In our ever-changing connected world, digital transformation is affecting every aspect of our lives. The automotive industry is no exception to this evolution: our cars are becoming our best co-pilots, allowing us to plan our trips with real-time data or read and respond to text messages using voice command.
Read more