Five key Cybersecurity takeaways for the automotive industry
News from industry experts to start driving your resilience

In our ever-changing connected world, digital transformation is affecting every aspect of our lives.
The automotive industry is no exception to this evolution: our cars are becoming our best co-pilots, allowing us to plan our trips with real-time data or read and respond to text messages using voice command.
This change is not only affecting our cars. The whole industry is augmenting its buses, trucks, tractors and supporting infrastructure with new functionalities, allowing them to become increasingly autonomous, connected, electric and shared.
More embedded in every piece of equipment, these new functionalities are also interconnected between each other and with other vehicles and road infrastructures.
This phenomenon is multiplying the entry points for potential attacks – each vehicle representing a larger risk surface – and increasing the threat level and the importance of the potential impacts.
Like other critical areas, the automotive industry faces safety consequences that include physical damage in addition to financial impacts.
Cyberthreat actors – ranging from States, criminal organizations or individuals – are becoming more sophisticated in order to reach their goals. Their objectives are to destabilize operations, increase their wealth via ransomware or theft, and modify vehicles to alter performance or functionalities, among others.
“Nearly every automotive manufacturer has been hacked” [1]
– Steve Tengler, Forbes
Given these rising challenges, regulating entities are acting to guide and empower Original Equipment Manufacturers (OEM) and suppliers to manufacture safe and sustainable vehicles with:
- UNECE WP.29 regulation R155 for Cyber Security Management System, and
- ISO/SAE 21434 for Road vehicles — Cybersecurity engineering.
Based on our experience in cybersecurity and in reference to these documents, we will discuss key takeaways to start preparing for cybersecurity engineering and augment your resilience against increasing cyber activity.
#1 – The stakes are not only in the long-term
With 86% of vehicles estimated to be connected in the global automotive market by 2025[2], the consideration of automotive cybersecurity cannot be mistaken as a futuristic concern.
While the risks increase with the growth of autonomous and connected vehicles, vulnerabilities already exist in the vehicles we use every day.
As early as 2015, cybersecurity researchers demonstrated that they were able to manage the air-conditioning of a Jeep Cherokee, but more dangerously, to take control of the braking and acceleration systems.
With more than 200 reported attacks in 2020, nearly 80% of which were remote[3], experts and hackers have demonstrated that the threats are to be reckoned with. Let’s not forget that the remaining 20% of attacks activated locally, with or without hacker intervention.
#2 – An impact on market access – a year from now
As mentioned, this past year, the automotive industry has seen new regulations and standards targeting the cybersecurity of the sector.
Since June 2020, the United Nations Economic Commission for Europe (UNECE) released the WP.29 regulation R155 for Cyber Security Management System. The UNECE document makes many references to the ISO/SAE 21434 standard, which will provide support for meeting the requirements of the regulation upon its release by the end of 2021.
As of June 2022, the requirements of the WP.29 R155 regulations will be non-negotiable for market access in the 56 member states of the UNECE, including Canada and the USA.
Such requirements include the management of cybersecurity measures for future vehicles by the OEM and sets expectations to retrofit these tools and techniques on earlier models in the upcoming years.
Regarding the ISO/SAE 21434 standard, while its purpose is not to legally bind industry actors, it is positioned to be a significant differentiator for the future of mobility. It will guarantee a high level of security for the vehicles or provide evidence that the vehicle has been developed in alignment with industry standards and best practices.
#3 – A responsibility throughout a vehicle’s lifecycle
In the ISO/SAE 21434 standard, which is intended to guide organizations through the processes they must follow to implement cybersecurity requirements, OEMs are responsible for the entire vehicle lifecycle: from the conception phase to decommissioning.
Since the average lifespan of a car is about 200,000 miles or 12 years[4], post-production processes such as software upgrades and incident response must be heavily considered.
The OEMs are not the only actors targeted in the document: suppliers will also need to comply with the security requirements.
To facilitate the management of such knowledge and data, the standard goes into detail regarding the governance aspects to take into account. The framework to implement includes suppliers and updates management, continuous improvement, risks assessments methodologies, etc.
#4 – The duty of fleet operators
From local buses and shared cars to cargo trucks, vehicle fleets can represent opportunities of interest for malicious groups. Especially amid the current pandemic, an attack could impact the distribution of medical supplies or vaccines.
Fleetwide cyber risks should be on the industry’s radar, especially for fleet operators that will have to incur the costs and operational impacts of service disruptions. From purchasing to day-to-day operations, fleet management teams have a role to play in ensuring a cybersecure industry.
As more and more buyers and managers of fleets of vehicles include cybersecurity requirements in their call for proposals, this heightened focus will significantly influence the overall security of our mobility. It will ensure cybersecurity requirements are met, evaluated but most importantly managed throughout the product lifecycle.
#5 – A golden rule: Do NOT pay the ransom
It may seem like a straightforward statement to make – but paying the ransom will only help perpetuate the risks of cyber-attacks, as it finances the criminal organizations. It is not a solution, as even after paying the ransom, you are not guaranteed that your organization will recover its data or goods.
Not paying the ransom means you need to be prepared in advance with the help of cybersecurity experts.
Assess your vulnerabilities
Whether you make or use vehicles, take the first steps towards resilient operations and vehicles with an assessment of your cybersecurity maturity. With the right experts, you will identify the gaps to fill in order to comply with the recent regulations and provide trustable experiences to your customers.
As a cybersecurity leader, the Thales multidisciplinary team based in Quebec can support you to assess, organize and implement a framework that fits your needs.
Towards a mobility you can trust.
This blog post is made possible by our great partner Thales as part of the Transportation Cybersecurity and functional safety Forum, an initiative of Propulsion Québec and supported by the Quebec government.
Continue reading on this subject

Will industrial strategies chart a new course for the future of Quebec industries?
The Quebec economy—and more broadly the world economy—faces multiple challenges: the climate crisis, supply chain problems, labour shortages, inflation, etc. Quebec has an abundant supply of resources, know-how, and expertise; however, the next points on its agenda should include structuring, developing, and planning industrial activities.
Read more
Telematic Data: the Key to a Successful Energy Transition
Fleet managers are currently facing the colossal challenge of the energy transition, in order to meet legislative requirements and societal demands. For most carriers, both in the passenger transport sector and in the last mile delivery sector, this green shift has already begun.
Read more
Ambition EST 2030 : a roadmap for propelling Quebec to the forefront of the electric and smart transportation industry by 2030
Propulsion Québec, the cluster for electric and smart transportation, is announcing Ambition EST 2030, a roadmap for the electric and smart transportation (EST) industry developed in partnership with Deloitte.
Read more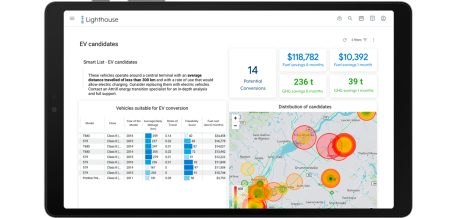
Energy transition, the challenge that is shaking up the trucking industry
The U.S. Department of Energy recently released a report containing a vehicle cost analysis for zero-emission medium and heavy-duty trucks.
Read more
The Mobility of the Future is Smart, Green, Inclusive and Healthy
Innovation is part of our Alstom in Motion 2025 strategy. It has brought us to where we are today, and we want to go even further. With the new scale and combined expertise, Alstom has doubled its innovation capacity and we will support this growth by doubling the financial investments in R&D, up to 600 million euros (875 million Canadian dollars) per year by 2024.
Read more
Astus – Proud to support IMPULSION MTL 2021
With more than 25 years of expertise in the field of vehicle telematics, Astus is now a key player in the energy and digital transition of mobility and transport.
Read more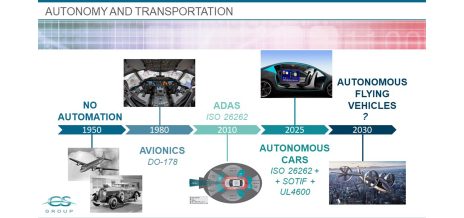
LiDAR and AI in autonomous vehicle commercialization and functional safety
The story of smart, autonomous transportation began nearly half a century ago. In the early 1980s, avionics systems started to replace more traditional mechanical and hydraulic systems through calculators and embedded software.
Read more
Is there a regulatory framework for location data?
Analysing location data can help service providers assess whether to boost services in one part of a city versus another, at a particular time of day or in preparation for an upcoming festival, for instance. However, the data used for these analyses is linked to individuals and makes it possible to identify them.
Read more
How to develop a successful strategy for your transition towards EVs
To this day, it is not uncommon to see a good number of companies relying on assumptions, sometimes non-global and inaccurate information reports in order to manage their vehicle fleet.
Read more
Why cyber hygiene should be a top priority
With cybercrime damages expected to cost the world $10.5 trillion annually by 2025, this evolving issue shouldn’t be taken lightly. Threat actors continue to develop new ways to attack organizations,
Read more